In everybody's life there is a time to change something. In my case UNIBIKE basic frame has been changed to the FELT Q720. Lets play with it :)
A few words about me, things I'm interested in and other more or less useful things...
Saturday, December 24, 2011
Friday, December 23, 2011
Monday, November 28, 2011
Wednesday, November 23, 2011
Saturday, November 5, 2011
The best of Bash.org.pl :)
absinth: omg
absinth: moj stary przeszedl cale call of duty
misiek: co w tym zlego lub dziwnego?
absinth: ta, ale on w przedostaniej misji sie mnieu pyta czy mozna colta na inna bron zmienic
absinth: moj stary przeszedl cale call of duty
misiek: co w tym zlego lub dziwnego?
absinth: ta, ale on w przedostaniej misji sie mnieu pyta czy mozna colta na inna bron zmienic
Sunday, October 23, 2011
Problem with installation of Windows Server 2008 R2 on VirtualBox
Sometimes I came across some strange problems which I dealt with easily after some time. One of them happened today. During installation of the Windows Server 2008 RC on the VirtualBox I saw the following screen.
Solution was simpler that I had thought before. I had to enable IO APIC :)
Simple? Really simple!
Solution was simpler that I had thought before. I had to enable IO APIC :)
Simple? Really simple!
VirtualBox is growing up :)
Well, well, well.... now we can say as was said by one of the greatest people: "Yes, we can" VirtualBox rules :)
Saturday, October 22, 2011
SAPD and service account password
As usually when it comes to the security subjects I'm under impression Paula Januszkiewicz's knowledge. And from time to time I try to check her methods to improve mine :)
Sometime in your system there are some services which are running on for example other user's account. When you go to the services console you can find some examples of it. In my example LC Remote Agent is working on Gerwazy account.
Gerwazy is the name of your friend's account and you (for some purposes) want to get password to it. What can you do? You can use the SAPD.exe which does it for you. So download it and try to run passing as the program's argument the service name.
Hmmm.... there is no secrets inside of the registry?? I know that they are, so why the application didn't display them? Maybe it should be run from the administrator account? Let's try.
Once again - no secrets. So maybe system account will be better (I'm sure it was written in the manual to the tool but I don't like reading the documents). How to be able to use this account? The simplest way - use psexec.
Voilà :) We've got the password :)
Sometime in your system there are some services which are running on for example other user's account. When you go to the services console you can find some examples of it. In my example LC Remote Agent is working on Gerwazy account.
Gerwazy is the name of your friend's account and you (for some purposes) want to get password to it. What can you do? You can use the SAPD.exe which does it for you. So download it and try to run passing as the program's argument the service name.
Hmmm.... there is no secrets inside of the registry?? I know that they are, so why the application didn't display them? Maybe it should be run from the administrator account? Let's try.
Once again - no secrets. So maybe system account will be better (I'm sure it was written in the manual to the tool but I don't like reading the documents). How to be able to use this account? The simplest way - use psexec.
Voilà :) We've got the password :)
Tuesday, October 11, 2011
psexec and winlogin
Since I knew who Paula Januszkiewicz is I have been under her impression. Today I watched her presentation from TechEd and I try to show some of her trick :)
The first is connected with winlogon - Paula shows that there is possible to get access to a administrator's PC without having their credentials. How? By using psexec. Its a tool which can leverage your credentials and make many impossible things real. The tool is written by Mark Russinovich - my personal God of Windows Internals :) So...
1. Download the tool and open the command line with the administrator privileges.
Of course you have got the UAT turned on so confirm the operation.
2. Go the the psexec directory and you may read the help about this great tool.
3. Enter the following command
About arguments you can real in the previously mentioned help :)
4. Lock the screen in normal way e.g CTRL+ L.
5. When locked screen is displayed, press ALT+TAB - you have got a command line. Run the explorer.exe and make fun with system account provileges :)
The first is connected with winlogon - Paula shows that there is possible to get access to a administrator's PC without having their credentials. How? By using psexec. Its a tool which can leverage your credentials and make many impossible things real. The tool is written by Mark Russinovich - my personal God of Windows Internals :) So...
1. Download the tool and open the command line with the administrator privileges.
Of course you have got the UAT turned on so confirm the operation.
2. Go the the psexec directory and you may read the help about this great tool.
3. Enter the following command
About arguments you can real in the previously mentioned help :)
4. Lock the screen in normal way e.g CTRL+ L.
5. When locked screen is displayed, press ALT+TAB - you have got a command line. Run the explorer.exe and make fun with system account provileges :)
Wednesday, October 5, 2011
Sunday, October 2, 2011
Gettings started with WinDGB
During the career path of every developer there is a time when he must get some new knowledge about something he has not been familiar with yet. Today came the time to use WinDBG. Basic configuration was shown on the page so there is no real need to copy it. Additionally you can download sosex library (and of course copy it to the WinDBG directory) from here.
To check your configuration you can do the following. I found the idea on the mgrzeg but it was so interesting that I had to check it by myself. Let me get you be familiar with it. A problem covered by the mgrzeg was connected with the security of strings which were being stored in the memory. As it is known, when you want to implement for example a form where an end user will be entered their credentials you will probably store the credentials as instance of the String class (or in case of some operation: StringBuilder class). Are you sure it is safe?
Here is a source code (a copy from the mgrzeg page) which give you the answer.
We have got here three functions. Fun1 creates some string and then appends to it numbers from the range of 0 to 4. According to the String class specification there is no possibility to append any characters to any object of String type so the results of the operation will be a set of different strings. Method called Fun2 uses the StringBuilder class. It is some better solution than using String but from security point of view there is the same issue. Fun3 uses SecurityString. It is really good (the best from the presented here) solution. Why? Compile the code and open the executable file in WinDBG.
Then let the program go to the ReadKey code - press F5 and after the have got the message "What do we have in memory?" press CTRL-C.
Now load necessary libraries and try to find the string from functions Fun1, Fun2 and Fun3.
As you can see despite the fact that we have got local variables inside of the Fun1 and Fun2, when we are in Fun3 these variables are available (in other words - not processed by GC yet) so an attacker with some knowledge can access to them. What about the variable from Fun3 method? It is unavailable :)
To check your configuration you can do the following. I found the idea on the mgrzeg but it was so interesting that I had to check it by myself. Let me get you be familiar with it. A problem covered by the mgrzeg was connected with the security of strings which were being stored in the memory. As it is known, when you want to implement for example a form where an end user will be entered their credentials you will probably store the credentials as instance of the String class (or in case of some operation: StringBuilder class). Are you sure it is safe?
Here is a source code (a copy from the mgrzeg page) which give you the answer.
We have got here three functions. Fun1 creates some string and then appends to it numbers from the range of 0 to 4. According to the String class specification there is no possibility to append any characters to any object of String type so the results of the operation will be a set of different strings. Method called Fun2 uses the StringBuilder class. It is some better solution than using String but from security point of view there is the same issue. Fun3 uses SecurityString. It is really good (the best from the presented here) solution. Why? Compile the code and open the executable file in WinDBG.
Then let the program go to the ReadKey code - press F5 and after the have got the message "What do we have in memory?" press CTRL-C.
Now load necessary libraries and try to find the string from functions Fun1, Fun2 and Fun3.
As you can see despite the fact that we have got local variables inside of the Fun1 and Fun2, when we are in Fun3 these variables are available (in other words - not processed by GC yet) so an attacker with some knowledge can access to them. What about the variable from Fun3 method? It is unavailable :)
Saturday, October 1, 2011
Is your Windows password really strong?
How to check if your password is really unbreakable? Simply - use Cain & Abel. It is software which is "easily downloadable from the Internet". So lets do it.
1. Open the Cain and go to the Cracker tab. Then check Import hashes from local system.
2. Highlight preferred account and choose NTLM hash breaking by using the brute force.
3. Enter key space and approximate maximal and minimal password length and start the attack.
Don't be scared if you see that you will have to wait about 13 years as it was in my case :) It is time which is needed to cover whole range of combination from the key set.
4. And after some time.... you have got it (or the better option for your password - you cannot find it despite you have been trying for very long time) :)
1. Open the Cain and go to the Cracker tab. Then check Import hashes from local system.
2. Highlight preferred account and choose NTLM hash breaking by using the brute force.
3. Enter key space and approximate maximal and minimal password length and start the attack.
Don't be scared if you see that you will have to wait about 13 years as it was in my case :) It is time which is needed to cover whole range of combination from the key set.
4. And after some time.... you have got it (or the better option for your password - you cannot find it despite you have been trying for very long time) :)
Thursday, September 29, 2011
CompTIA Security+ passed :)
Today is a great day :) I have dealt with the CompTIA Security+ exam. It was easiest than I had thought before but I took a few nights without sleeping. But I managed finally. What have I been learning for it? First of all CBT Nuggets series. It covers almost all what you need to know when it comes to this exam. And of course I suggest going through the examcollection.com site for being sure you are able to pass it.
My helpers for the exam. Enjoy and pass it :)
Sunday, August 28, 2011
Monday, August 15, 2011
Google search reference :)
Don't know how to search the Google for specific results? Don't worry. Look at this :)
Link
Link
Saturday, August 6, 2011
Duplicated UUIDs for Virtual Box HDs
Simply, invoke the commane:
VBoxManage internalcommands sethduuid WinXPCl2.vdi
VBoxManage internalcommands sethduuid WinXPCl2.vdi
Saturday, July 30, 2011
Set a GRUB menu background...
It's time to make my (and maybe your) Debian system more beautiful. It's a pretty simple action but the effect is really good. So (as my boss usually says especially when we don't have more subjects to be talked about:)) - GO TO WORK!
1. Prepare a splash image by doing one of the following actions:
- install a splash images collection
- prepare your own image according to the rules (og course in the GIMP software)
2. Open the grub_background.sh file in your favorite editor (of course in the Vi:))
3. Enter the full path to your image in the first line of the script
4. Save the file, update the grub and reboot the system.
5. The result in my system looks like the following one.
1. Prepare a splash image by doing one of the following actions:
- install a splash images collection
- prepare your own image according to the rules (og course in the GIMP software)
2. Open the grub_background.sh file in your favorite editor (of course in the Vi:))
3. Enter the full path to your image in the first line of the script
4. Save the file, update the grub and reboot the system.
5. The result in my system looks like the following one.
Wednesday, July 20, 2011
How to adjust date and time in machine running on Virtual Box?
VBoxManage modifyvm Win7 --biossystemtimeoffset $[($(date -d '2011-07-20 11:00:00' +%s)-$(date +%s))*1000]
:)
:)
Sunday, July 17, 2011
Is the Facebook safe place?
(followed by Devil's Blog on Security)
At the beginning I'd like to inform that goal of this material is not to encourage anyone to get somebody else credential to his Facebook account. It should only show that the Internet is not a safe place and utilizing of public computers can end in more or less harmful way. This scenario is simplified due to the fact that it should only show some things and not provide solution for cyber criminals.
1. Open the Wireshark and start capturing packets.
2. Open you browser, go to the Facebook web page and log into it.
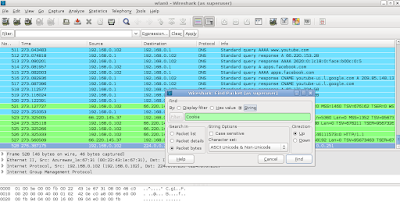
3. Stop capturing the packets by the Wireshark and look for a Cookie string inside of the captured contents (Ctrl+F will be helpful...)
4. When you find the contents like this, copy the value of Cookie variable to the any notepad.
5. Open N Edit and add each of variables stored in your notepad separately. For example for xs variable you should do like this shows
6. At the end open the browser on the main Facebook page - you are logged in without asking about any credentials.
If you are working on a Windows machine, you can ommit the Wireshark section and use the script written by Marcus Murray (I've done only some little changes inside of it) which looks like
ngrep -d 1 -W byline "Host: www.facebook.com|Cookie:" | findstr "^Cooki
e:"
It shows cookies information for all sessions connected to the Facebook (of course ngrep and wpcap should be installed on the machine).
Enjoy!
At the beginning I'd like to inform that goal of this material is not to encourage anyone to get somebody else credential to his Facebook account. It should only show that the Internet is not a safe place and utilizing of public computers can end in more or less harmful way. This scenario is simplified due to the fact that it should only show some things and not provide solution for cyber criminals.
1. Open the Wireshark and start capturing packets.
2. Open you browser, go to the Facebook web page and log into it.
3. Stop capturing the packets by the Wireshark and look for a Cookie string inside of the captured contents (Ctrl+F will be helpful...)
4. When you find the contents like this, copy the value of Cookie variable to the any notepad.
5. Open N Edit and add each of variables stored in your notepad separately. For example for xs variable you should do like this shows
6. At the end open the browser on the main Facebook page - you are logged in without asking about any credentials.
If you are working on a Windows machine, you can ommit the Wireshark section and use the script written by Marcus Murray (I've done only some little changes inside of it) which looks like
ngrep -d 1 -W byline "Host: www.facebook.com|Cookie:" | findstr "^Cooki
e:"
It shows cookies information for all sessions connected to the Facebook (of course ngrep and wpcap should be installed on the machine).
Enjoy!
Incompatible extension to Firefox
When I tried to install N Edit to my Iceweasel, the message as the following one appears.
This tool is really important from my point of view so I start to look the solution of the problem. And I got it! So
1. Download the extension to local disk.It's a zip format so after you click on the xpi file two times you will see the contents of it.
2. Edit the highlighted line by entering the proper version of your browser.
3. Save the file. Your system should ask you if you want to update the contents of the zipped file so that you should have the xpi file with your changes.
4. Right click on the xpi file and choose "Open with...". Select you browser and when the windows pops up, confirm the installation of the extension.
5. Restart your browser and make fun :)
This tool is really important from my point of view so I start to look the solution of the problem. And I got it! So
1. Download the extension to local disk.It's a zip format so after you click on the xpi file two times you will see the contents of it.
2. Edit the highlighted line by entering the proper version of your browser.
3. Save the file. Your system should ask you if you want to update the contents of the zipped file so that you should have the xpi file with your changes.
4. Right click on the xpi file and choose "Open with...". Select you browser and when the windows pops up, confirm the installation of the extension.
5. Restart your browser and make fun :)
Saturday, July 16, 2011
Recover debian root password.... :)
1. Restart the system.
2. During booting when a windows similar to the following one appears press E key.
Appears things as in the screen.
3. Change the line starts with linux /boot... in the way shown below
4. Ctrl+X to boot the system. The console appears with the rool privileges which allows you to change the password.
To prevent this kind of situations you can set a password for the boot loader. Detailed description was posted on ubuntuforums.org so I won't explain it. I'll show only how this operation looks like.
1. Open the 00_header file
2. Add the highlighted line at the end of it. These lines contain user name and user password which the system will be asked for when you are trying to modify the boot menu
3. Save the file, update the grub and reboot the system.
4. After the grub menu is displayed, press 'e' to edit the selected boot entry.
5. The system prevents from editing the entries by asking for the credentials entered before.
6. After correct authentication you will be able to change the boot entries.
But when you secure your Debian system in this way, there is possible to crack it anyway. How? By using a bootable CD/DVD with some linux distribution :)
Enjoy:)
2. During booting when a windows similar to the following one appears press E key.
Appears things as in the screen.
3. Change the line starts with linux /boot... in the way shown below
4. Ctrl+X to boot the system. The console appears with the rool privileges which allows you to change the password.
To prevent this kind of situations you can set a password for the boot loader. Detailed description was posted on ubuntuforums.org so I won't explain it. I'll show only how this operation looks like.
1. Open the 00_header file
2. Add the highlighted line at the end of it. These lines contain user name and user password which the system will be asked for when you are trying to modify the boot menu
3. Save the file, update the grub and reboot the system.
4. After the grub menu is displayed, press 'e' to edit the selected boot entry.
5. The system prevents from editing the entries by asking for the credentials entered before.
6. After correct authentication you will be able to change the boot entries.
But when you secure your Debian system in this way, there is possible to crack it anyway. How? By using a bootable CD/DVD with some linux distribution :)
Enjoy:)
Subscribe to:
Posts (Atom)